Access As a Service
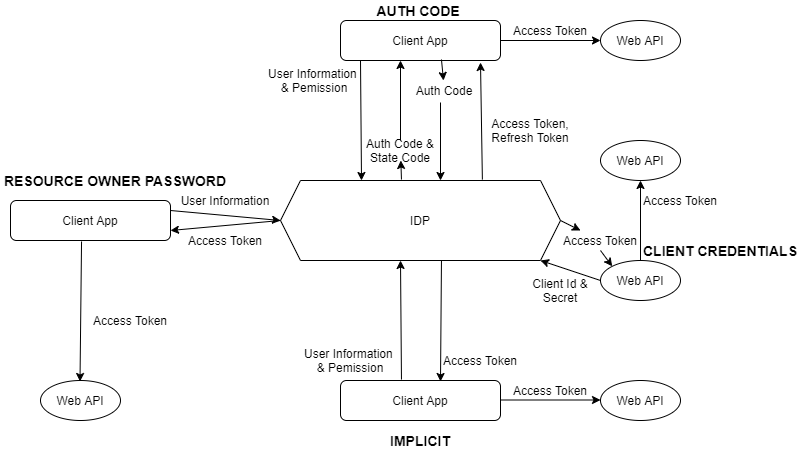
As part of our needs, we are using a different kind of application. Each application has a different kind of login mechanism. Each mechanism will enhance user experience like federated login with an external provider and improve the application security like adding a verification layer as part of user login. Most of the applications are stateless and they are accessing their backend APIs using an access token. This access token should have information about the user access, minimal user information and it should expire as per the security needs. We can generate the access token in different ways using different types of grant types.
ClientCredientials:
This type of grant is commonly used for server-to-server interactions that must run in the background, without immediate interaction with a user. Multiple application they can communicate with each other using this flow. They will pass their client id and the secret to the IDP and get the token. Using that token they will access the partner APIs.
Resource Owner Password:
The client needs to send the client id and user credentials to IDP and then receive the token. Using the token they can access the API. Most of the applications using this approach.
Implicit:
The client needs to send the client id, user credentials, and list of permission they want to grant to IDP and then receive the token. Using that token they can call the API with limited access. This is mainly used to login with an external provider. User needs to login with their external identity provider using OpenIDConnect protocol.
Authorization Code:
It will add one more layer to the implicit flow. Instead of returning the token, it will return the authorization code. The client application needs to send the authorization code to get the access token. Using this they can access the APIs.

Comments
Post a Comment